Year in Review: OONI in 2021
In light of the ongoing global COVID-19 pandemic, 2021 continued to be a challenging year for everyone.
Yet, several exciting things happened in the censorship measurement world. In this post, we share some OONI highlights from 2021, as well as some upcoming OONI projects for 2022!
OONI Probe
Automated OONI Probe testing
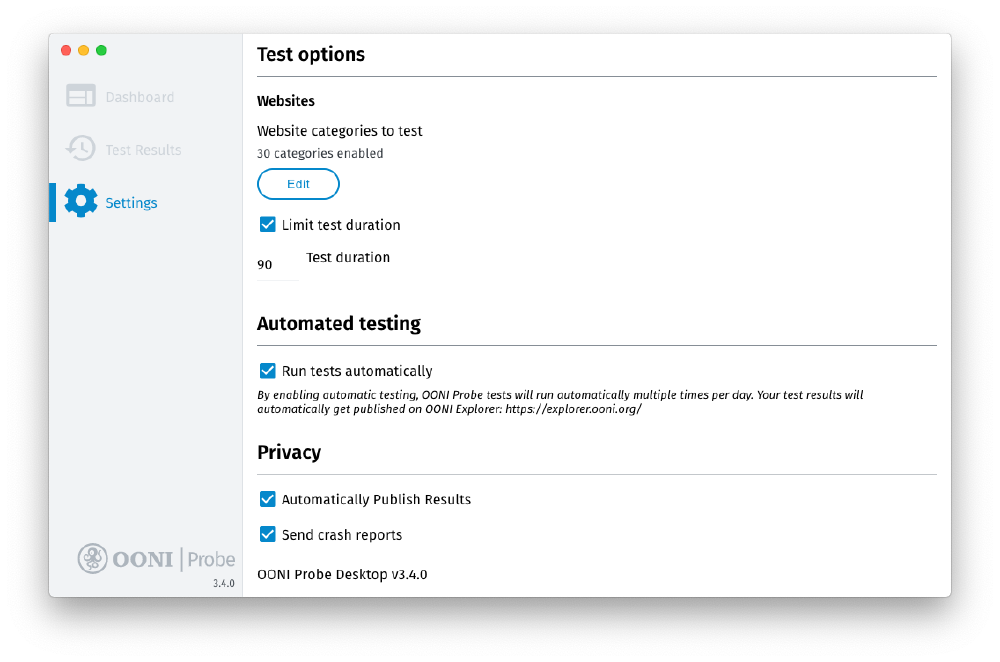
Would you like to measure internet censorship every day without having to remember to manually run tests? You can now have OONI Probe run regular censorship measurement tests automatically for you!
In 2021, we added support for automated testing to both the OONI Probe mobile and desktop apps. This means that you can configure your OONI Probe app to run tests automatically on a regular basis, without having to remember to actively run the tests yourself.
All you need to do is enable the “Run tests automatically” option in the “Automated testing” setting of your OONI Probe app. Through these settings on OONI Probe Mobile, you can choose whether you’d prefer to have OONI Probe only run tests while you’re connected to WiFi and when your phone is charging (to avoid consuming your data and battery).
Depending on the OONI Probe platform, automated testing currently differs a bit. If you enable automated testing on OONI Probe Android, iOS, Windows, or macOS, all tests are run automatically every hour. If you enable automated testing on OONI Probe Linux, automated testing is performed every 12 hours. In all cases, the testing includes all tests currently shipped as part of the OONI Probe apps, excluding the performance card tests (which are bandwidth intensive) and the new experimental card tests. Website testing is currently limited to 100 URLs in each automated run, which are randomly selected from the Citizen Lab test lists.
To avoid over-cluttering the “Test Results” section of your OONI Probe app with too many test results (from automated runs), they are only made available on the OONI API and OONI Explorer, where they are openly published in real-time.
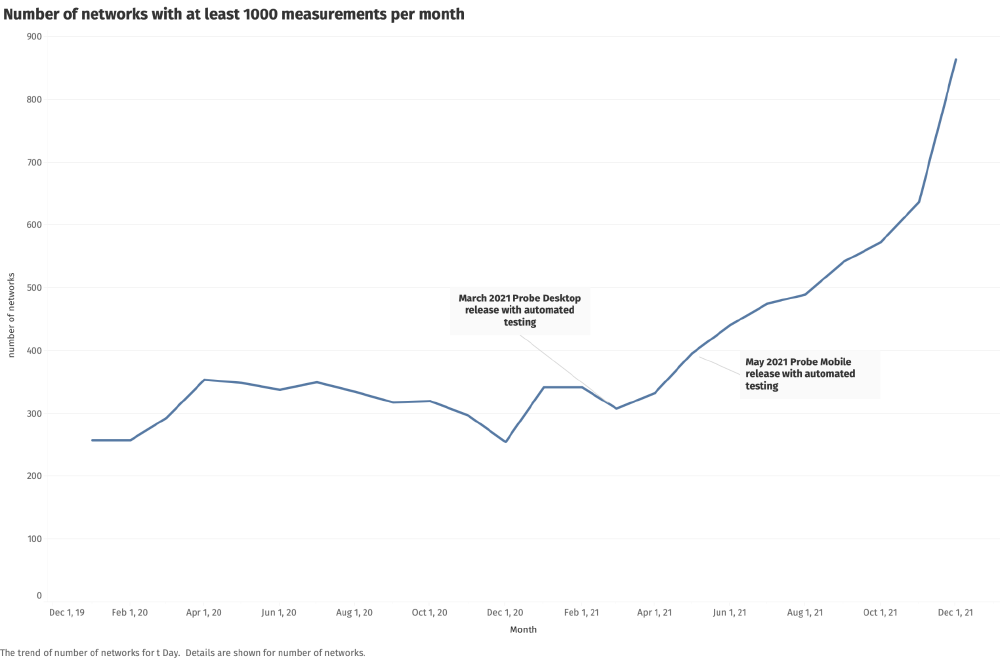
Since the release of OONI Probe versions with support for automated testing, we have observed a spike in OONI measurement coverage worldwide. Notably, we observe a spike in the number of ASNs that receive at least 1,000 OONI measurements every month, as illustrated below.
The above graph demonstrates that automated OONI Probe testing has helped ensure that a larger volume of measurements is collected from a larger set of stable vantage points over time.
We strongly recommend enabling automated testing, as this will help ensure regular testing, which is crucial for detecting censorship events. In doing so, you will contribute open data and help the internet freedom community monitor and respond to censorship events around the world.
New Debian package for OONI Probe
We released a new Debian package for OONI Probe with support for automatic testing.
As part of the installation process, this package displays the informed consent procedure through the use of native Debian packaging features. Packages are automatically built as part of the continuous integration workflow. You can get the new Debian package through the OONI Probe installation page for Linux.
New OONI Probe Command Line Interface for Linux and macOS
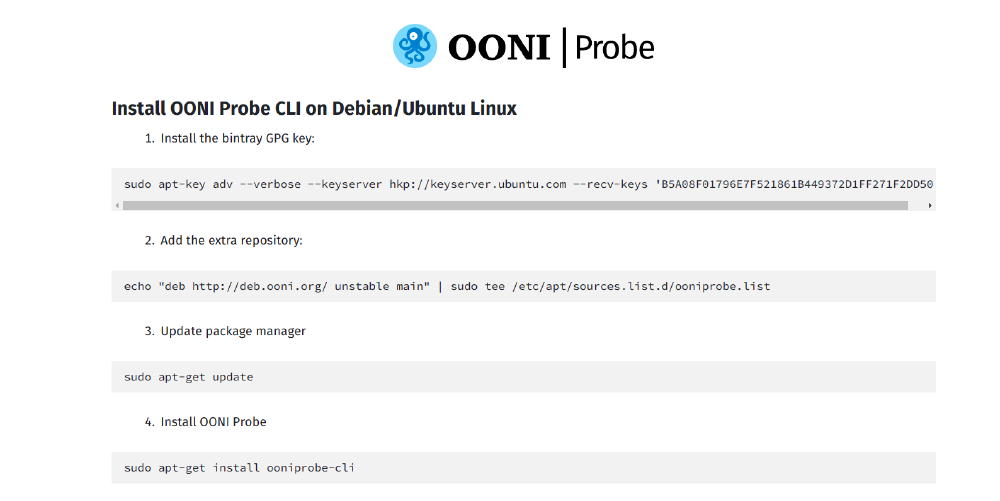
We released a new OONI Probe Command Line Interface (CLI) for Linux and macOS. You can also run OONI Probe CLI on Raspberry Pis.
OONI Probe CLI serves as a replacement for the python legacy version of ooniprobe, which has been around since 2012, and which (to our surprise!) is still being run by users around the world.
If you happen to be one of those users, please switch over to OONI Probe CLI because:
Legacy ooniprobe will no longer be able to contribute measurements, since it relies on v2 onion services which were deprecated in October 2021;
OONI Probe CLI regularly runs all tests automatically in the background;
OONI Probe CLI will receive important future updates (new tests, code improvements, etc.).
You can install OONI Probe on the command line on:
Upon installation, OONI Probe will run tests automatically every day! Given that all OONI Probe measurements are openly published in real-time, you will help the internet freedom community better investigate internet censorship around the world.
New OONI Probe Experimental card
As censorship becomes more sophisticated, we need to ship new censorship detection tests faster.
To this end, we added a new Experimental card to the OONI Probe apps, where we plan to release our latest experiments. This card is meant to provide us agility in adding and removing new experiments on an ongoing basis, particularly in response to emergent censorship events. By having a relatively quick and easier way to ship new experiments, we aim to collect relevant network measurement data that can help us improve our methodologies and respond faster to more sophisticated forms of internet censorship.
Through the Experimental card, you can currently run our new STUN reachability test. In 2022, you can expect to see new experimental tests!
Improved resilience to blocking
At some point in 2021, community members in Iran and a few other countries reported that they were unable to use OONI Probe. We investigated the issue and worked towards making OONI Probe Android more resilient to accidental or deliberate blocking of our backend services.
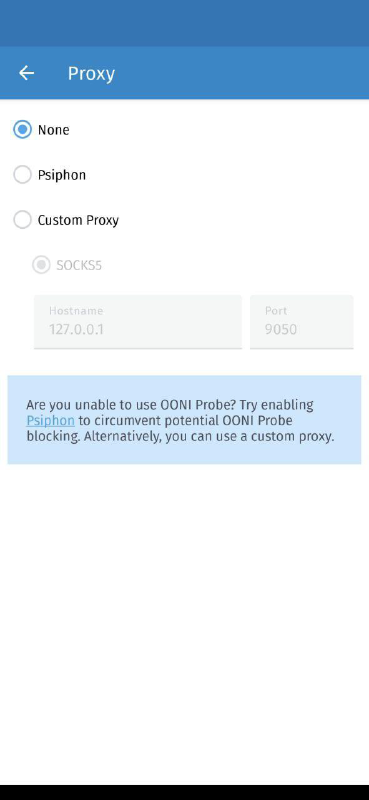
Specifically, we implemented support for specifying a proxy that speaks with OONI’s backend services. We also improved the build process to influence the TLS Client Hello fingerprint, which helps with avoiding accidental blocking.
OONI Probe Android now includes backend proxy settings where you can:
Enable Psiphon, or;
Use a custom proxy.
This will help with circumventing any accidental or deliberate OONI Probe blocking.
We published a blog post where we describe in detail what we did to make OONI Probe Android more resilient.
New OONI Probe user guides
Do you have questions about using OONI Probe? To support community use of OONI Probe and community engagement activities, we published 3 new OONI Probe user guides in 2021.
These include user guides for:
OONI Probe Mobile (Android & iOS)
OONI Probe Desktop (Windows & macOS)
OONI Probe Command Line Interface (Debian/Ubuntu Linux, macOS, Raspberry Pis)
These user guides share step-by-step instructions (with screenshots) on how to:
Install and run OONI Probe (to measure various forms of internet censorship)
Access and share OONI censorship measurement data
Customize your use of OONI Probe (for example, to test websites of your choice)
Configure your OONI Probe settings
With our new user guides, you can become an OONI Probe power user! Upon reading these guides, we hope you feel empowered to share your OONI Probe knowledge and skills with others.
Measurement methodologies
New OONI Probe test for Signal Private Messenger app
Signal Private Messenger, commonly used by human rights defenders worldwide, is widely considered the state-of-the-art app for private and secure communications. But as its popularity surged recently, we started to hear that it was blocked in several countries.
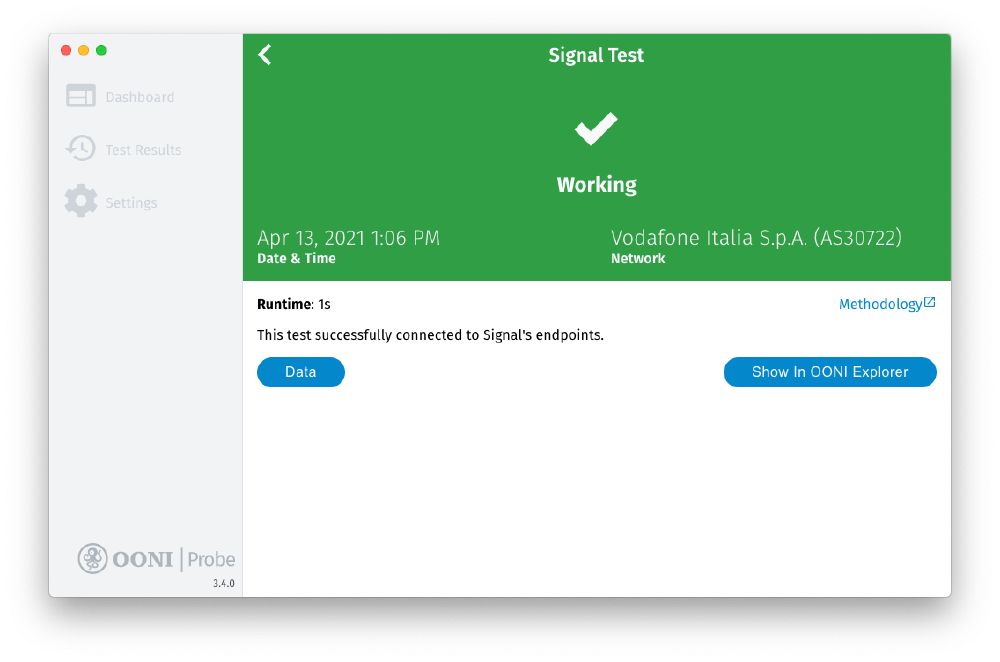
In response to community requests, we released a new OONI Probe test designed to measure the blocking of the Signal Private Messenger app.
Specifically, our new Signal test checks whether it’s possible to establish a TLS connection (while validating the TLS certificate against the custom Signal CA root certificate) and send an HTTP GET request to the Signal server backends from the vantage point of the user. If the test successfully performs an HTTPS request to the tested Signal endpoints, the Signal app is considered reachable from the tested network. However, if connections to any of the tested Signal endpoints fail, Signal might be unreachable or blocked.
You can run this test and measure the reachability of the Signal app through both the OONI Probe mobile and desktop apps. All Signal test results from around the world are openly published in real-time, enabling the internet freedom community to track whether access to the Signal app is being interfered with.
Based on Signal test results contributed by our community worldwide, we published a research report which documents the blocking of the Signal app in Iran, China, Cuba, and Uzbekistan.
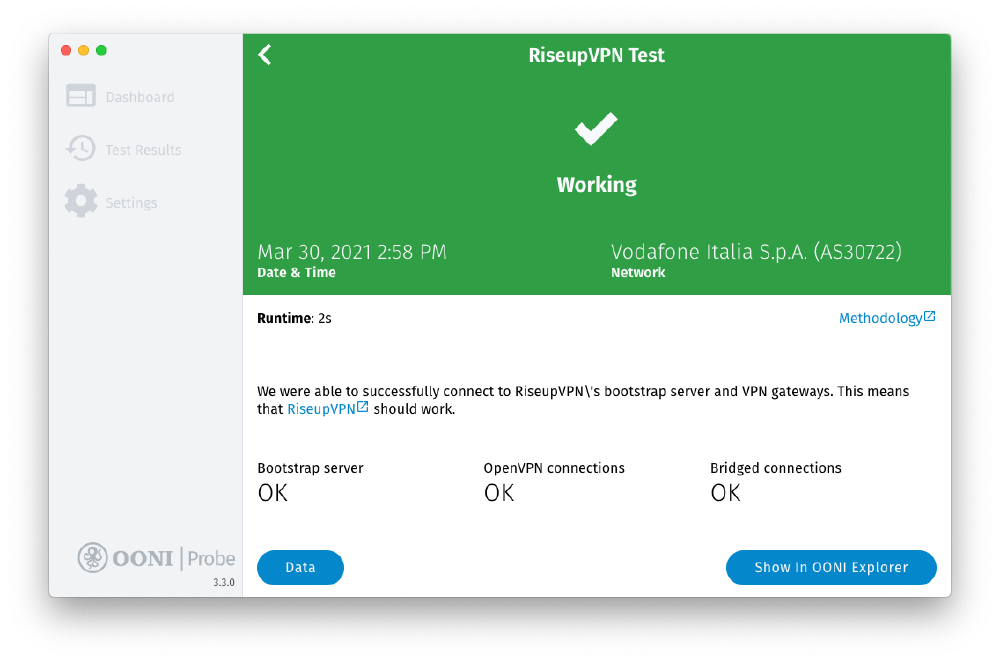
New OONI Probe test for RiseupVPN
Thanks to the LEAP collective, the OONI Probe apps include a new test for measuring the blocking of RiseupVPN!
The RiseupVPN test, developed by the LEAP collective, provides an automated way of examining whether RiseupVPN works on a tested network. Specifically, this test evaluates if the bootstrap servers used during the self-configuration of the VPN clients can be reached. The test also checks if RiseupVPN’s gateways can be reached on different ports and transports. In the future, this test can form the base to offer a generic way to probe the reachability of other LEAP-powered VPN infrastructure, self-hosted by other providers.
You can now check whether RiseupVPN works on your network by running OONI Probe. All RiseupVPN test results from around the world are openly published in real-time.
New OONI Probe tests in progress
Throughout 2021, we worked on designing and developing new OONI Probe experiments which we plan to ship as part of the OONI Probe apps in 2022.
The new tests include:
We share further information below.
Website measurement test
Currently, when you measure the blocking of websites with OONI Probe, you run the OONI Web Connectivity test. We released this test back in 2016, when the web was quite different. We therefore decided to re-think how we measure websites, and to write a brand new experiment for measuring the blocking of websites.
Our new experiment (tentatively called “Websteps”) will serve as the successor to our Web Connectivity experiment. The research question that this experiment tries to address is that of enumerating all the possible ways by which a specific URL can be blocked. This means that this experiment does not stop when it detects the first type of blocking, but rather drills deeper to discover all the ways by which blocking is implemented.
The main differences compared to our current Web Connectivity test that are worth highlighting include:
We use a new test helper mechanism for enumerating all the endpoints that need to be tested for a target URL. This includes all the IPs that a particular domain resolves to, as well as the full redirect chain from an uncensored vantage point.
We also use QUIC to measure websites.
We expand the taxonomy for classifying the various means by which blocking is implemented.
We add support for measuring all IP:URL pairs to detect IP blocking that only targets certain addresses.
In writing this new test, we also made significant improvements to our measurement engine. In particular, we implemented several new primitives for performing the various stages of a URL request (that can eventually be reused by other tests as well). In doing so, we also documented (in our tutorial on writing OONI Probe tests) how third parties can go about using these functions for writing their own tests. Once the improvements to the measurement engine were made, we wrote the new implementation of Websteps using these new functions.
During the summer of 2021, we had the opportunity to serve as the host organization for Google Summer of Code (GSoC) student, Kathrin Elmenhorst, who worked with us on developing OONI Probe network experiments. We worked with Kathrin on implementing a prototype for the new Websteps experiment, adding support for using the utls library for TLS parroting, and making improvements to how errors are handled inside of our measurement engine.
Currently, you can run the new Websteps experiment through our miniooni researcher tool. We plan to ship this new test as part of the OONI Probe apps in 2022!
Tor Snowflake pluggable transport test
We developed a new experiment for measuring the reachability of the Tor Snowflake pluggable transport, which is used by Tor users in censored environments. In particular, Snowflake is a pluggable transport that proxies traffic through temporary proxies using WebRTC.
Apart from developing the new OONI Probe experiment for Tor Snowflake, we also integrated Snowflake into OONI Probe as a Go library leveraging version 2 of the pluggable-transports specification. We expanded our data analysis capabilities to process and annotate Snowflake measurements as “anomalous” when the test fails to successfully bootstrap the Snowflake pluggable transport, and we added support for extracting the bootstrap time of the Snowflake experiment. We also added support to OONI Explorer and to the OONI API for displaying measurements collected from our new Snowflake experiment.
We plan to ship the new Tor Snowflake experiment as part of the OONI Probe apps in 2022!
New tutorial for writing OONI Probe tests
Are you interested in contributing your own test to OONI Probe?
We published a new tutorial which explains how to write OONI Probe tests.
This in-depth tutorial is meant for developers who are interested in contributing new experiments to OONI Probe. The tutorial includes multiple chapters that explain how to practically write a network measurement experiment (using the Tor Snowflake experiment as an example), how to use the measurex package to write network experiments, and how to use the netxlite networking library. The tutorial includes code based on existing network measurement experiments.
OONI Probe has always been free and open source to encourage independent third-party review of our methodologies. We have always hoped that the openness of OONI Probe would also encourage talented developers to contribute new experiments.
Now, with the help of our new tutorial, you can contribute your own network measurement tests. If integrated into OONI Probe, your test will be run in around 200 countries and territories every month, with test results published as open data in real-time.
We have already integrated the RiseupVPN test developed by the LEAP collective, and we have worked with M-Lab on integrating the NDT and DASH performance tests. We look forward to integrating more tests from the community!
New OONI tools in progress
Throughout 2021, we worked on developing the following new OONI tools:
OONI Probe Web
Web platform for updating test lists
Measurement Aggregation Toolkit (MAT)
We plan to publicly launch the above tools in 2022! Below we share information about each tool.
OONI Probe Web
Throughout 2021, we worked on building a new OONI Probe Web version designed to run from your web browser. Since this does not require the installation of software, OONI Probe Web is meant to support rapid response efforts to emergent censorship events.
Over the years, we have received many community requests for a browser-based version of OONI Probe that community members can easily share, and which does not require the installation of a new app. In response to these requests, we are building OONI Probe Web, but it will not serve as a replacement for our OONI Probe apps because the types of tests that you can run from a browser are very limited in comparison to what you can technically measure through an application. As a result, OONI Probe Web is limited to website testing (unlike the OONI Probe apps which include a variety of different tests).
OONI Probe Web is therefore meant to supplement the OONI Probe apps, to serve as a gateway for introducing more people to OONI Probe, and to encourage more OONI Probe app installations.
We have a prototype of OONI Probe Web ready, and we plan to publicly launch it in 2022!
Web platform for updating test lists
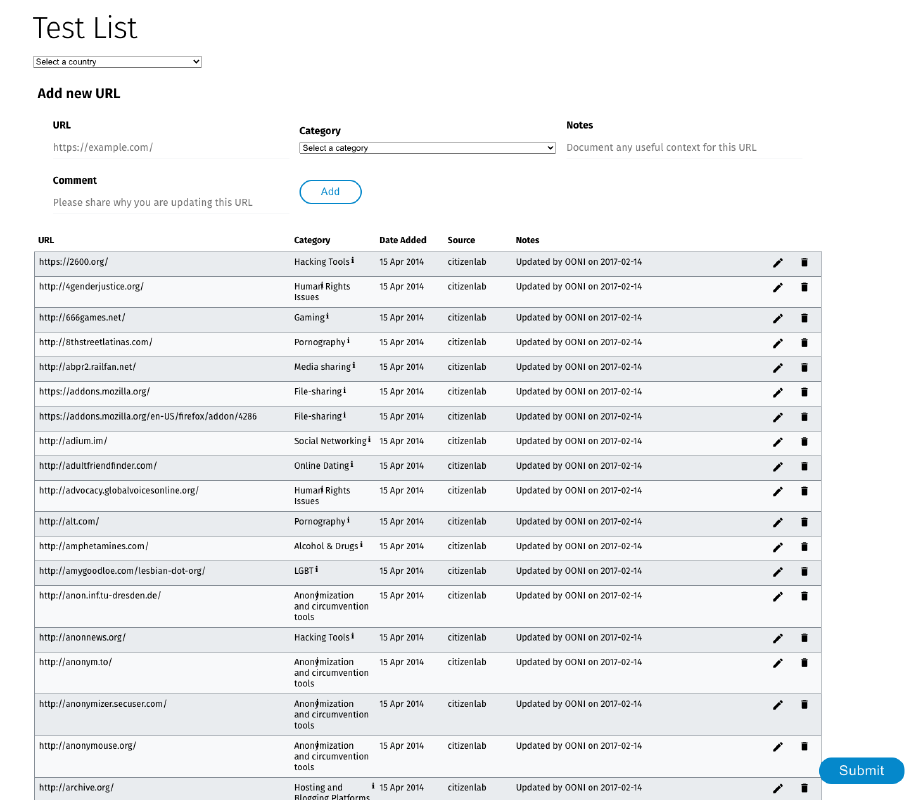
When you measure the blocking of websites with OONI Probe, you test websites included in the Citizen Lab test lists. Given that OONI Probe website testing is limited to the specific websites included in these lists, the quality of OONI website censorship measurement findings greatly depends on the quality of the websites included in the Citizen Lab test lists.
These lists are publicly hosted on GitHub, and are curated and updated by community members around the world. However, many community members who are best suited to determine which websites should be tested for censorship (such as political scientists and human rights defenders) are not GitHub users (a platform typically used by developers), which has presented challenges in updating the Citizen Lab test lists.
We therefore developed a new web platform to enable community members to review and contribute to the Citizen Lab test lists without using GitHub. Through this web platform, you will be able to review all the Citizen Lab test lists, add new URLs, propose the deletion of URLs, and edit existing URLs and category codes. You will be able to submit your contributions directly through the web platform, which will automatically open a pull request for you on GitHub so that community contributions can continue to go through the usual peer-reviewed process.
We currently have a private beta version of the web platform ready, which we’re improving upon based on community feedback. We aim to publicly launch the platform in 2022!
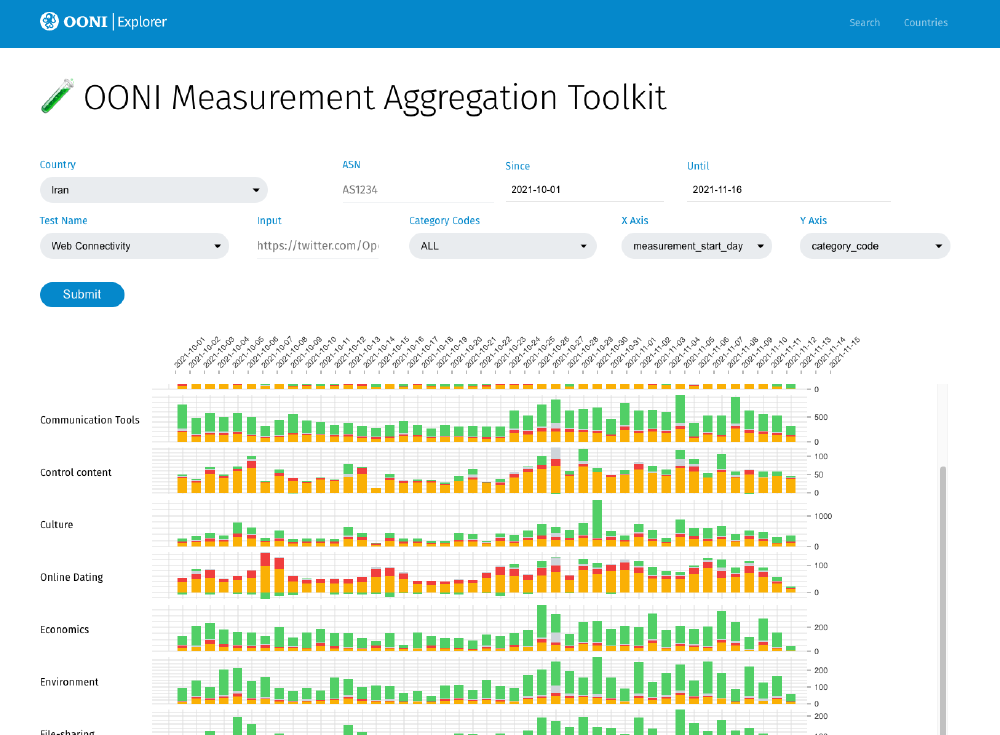
Measurement Aggregation Toolkit
Evaluating internet censorship requires examining measurements in aggregate, which is why we are building a new Measurement Aggregation Toolkit (MAT).
As part of our OONI data analysis efforts (which, for example, support our research reports), we always aggregate measurements to evaluate whether “anomalies” (signs of potential censorship) are present and, if so, whether we observe a large volume of anomalies (on a specific network) in comparison to successful measurements. Viewing OONI measurements in aggregate not only helps with ruling out false positives and better detecting censorship events, but it also helps with evaluating how censorship changes over time, and how it differs across networks in a country.
Given that data aggregation is essential for evaluating and detecting censorship events, we decided to automate this process to enable the broader internet freedom community to more effectively monitor and respond to censorship events based on OONI data.
With our new Measurement Aggregation Toolkit (MAT), you will be able to produce custom charts based on aggregate views of real-time OONI data collected from around the world. We are still working on improving the MAT, but we expect to publicly launch it in 2022!
Real-time analysis and URL prioritization
All OONI measurements collected from around the world are openly published in real-time.
We are now in a position to automatically confirm instances of DNS-based censorship (when block pages are served). We added backend support for confirming DNS-based anomalies, and we added new blockpage fingerprints (both DNS and HTTP response body) to our database. This has allowed us to automatically detect and confirm the blocking of many more websites around the world. OONI Explorer now displays many cases of automatically confirmed DNS-based censorship from countries that include Malaysia, Thailand, and Myanmar.
To improve the quality of website testing (and resulting OONI measurements), we are actively using our smart URL list system to adjust URL testing priorities worldwide, particularly in response to emergent censorship events. In particular, we are actively using (and improving upon) the OONI check-in API to orchestrate automated OONI Probe testing (if a user has enabled automated testing), and to ensure that probes measure URLs based on our prioritization policies configured in the backend.
Based on our smart URL list system, we have prioritized the global testing of specific social media URLs which are frequently blocked around the world. We also prioritize the testing of the Citizen Lab’s “Social Networking (GRP)” category code in specific countries in response to reports involving the blocking of social media websites.
Our new smart URL list system has empowered us to dynamically adjust URL testing priorities in response to censorship events. On 14th July 2021, for example, we bumped up the priority of the Citizen Lab’s “Social Networking (GRP)” category code in Cuba (in response to reports of social media blocks amid protests). This enabled us to detect (and collect measurements on) the temporary blocking of facebook.com and tiktok.com in Cuba (in addition to the blocking of other social media apps). Following the prioritization of URLs from this category, we were able to collect (and publish) a total of 960 measurements pertaining to the testing of social media URLs in Cuba during the protests.
Throughout 2021, we made a series of improvements to the OONI data processing pipeline, we re-processed all OONI measurements, we added scoring for new experiments, and we started migrating over to alternative database solutions that boost the performance of our services and better meet our data needs.
Research reports
In collaboration with community members, we published the following 10 research reports documenting internet censorship events around the world:
How countries attempt to block Signal Private Messenger App around the world
Media censorship in Azerbaijan through the lens of network measurement
Myanmar: Data on internet blocks and internet outages following military coup
Uganda: Data on internet blocks and nationwide internet outage amid 2021 general election
Notably, we had the opportunity to collaborate with IODA, Kentik, and other researchers from UC San Diego and the University of Michigan on a research paper (“A multi-perspective view of Internet censorship in Myanmar”) which offers a holistic view into the censorship events that followed the February 2021 military coup in Myanmar. We submitted this paper to the ACM SIGCOMM 2021 Workshop on Free and Open Communications on the Internet (FOCI 2021), who published our paper in August 2021.
We also submitted a research paper (“Measuring DoT/DoH Blocking Using OONI Probe: a Preliminary Study”) to the 2021 DNS Privacy Workshop of the NDSS Symposium, where we present our new DNSCheck experiment and measurement results from the testing of 123 DoT/DoH services (corresponding to 461 TCP/QUIC endpoints) in Kazakhstan, Iran, and China.
In December 2021, we started serving as the host organization for Gurshabad Grover, an Open Technology Fund (OTF) Information Controls Research Fellow who will investigate how ISPs, through their technical decisions, can exacerbate or minimize the effects of state-ordered censorship (with a focus on South Asia and Southeast Asia). We also look forward to hosting two other OTF research fellows in 2022!
Community
OONI partnerships
Since 2016, we have had the opportunity to form partnerships with 41 organizations from around the world on the study of internet censorship.
Throughout 2021, we formed several new partnerships, including those with Internet Society (ISOC), Tanzania’s Zaina Foundation, and India’s Centre for Internet and Society (CIS). We continued to collaborate with our partners primarily through the coordination of censorship measurement efforts, training, and by providing OONI data analysis support.
OONI Partner Training 2021
To connect with our current (and prospect) partners, we organized and hosted two 3-day online OONI Partner Training events:
1st OONI Partner Training (28th-30th June 2021): Participants from Africa and Latin America
2nd OONI Partner Training (5th-7th July 2021): Participants from Asia and the Middle East
Overall (as part of the 2 events), we had the opportunity to facilitate OONI training for 86 participants who work with 49 digital rights organizations around the world. Many of the participants work with local/regional digital rights organizations in 25 countries, while other participants work internationally with human rights organizations and circumvention tool projects.
The goal of the OONI Partner Training was to share knowledge and skills on OONI’s censorship measurement tools, dataset, and methodologies to enable their use as part of research and advocacy efforts. We also aimed to collect feedback on how to improve OONI tools to better serve community needs.
The event was facilitated entirely online and entailed two 1.5 hour sessions per day (over 3 days). We facilitated the following 6 sessions as part of each of the two (3-day) OONI Partner Training events:
Information Controls Around the World
Introduction to Internet Censorship (slides)
Using the OONI Probe Apps
Using OONI Run to coordinate censorship testing
Using OONI Explorer to find censorship measurement data
Interpreting OONI data (slides)
As an outcome, participants gained knowledge and skills necessary for carrying out – and engaging their communities with – OONI censorship measurement research and advocacy. We also had the opportunity to collect extremely useful feedback from participants on how to improve OONI tools, data, and methodologies. We share further information about the training sessions and overall event through our relevant blog post.
OONI workshops and presentations
In light of the COVID-19 pandemic, most conferences and events continued to be hosted online this year.
Throughout 2021, we presented OONI at many (online) conferences and events, including:
State of the Onion 2021. During the Tor Project’s annual State of the Onion 2021 event, we shared OONI highlights from 2021, as well as upcoming OONI projects for 2022.
ISOC Community Week 2021. On 16th November 2021, we presented OONI as part of the Internet Society’s (ISOC) Community Week event.
Swahilipot Hub event for HacktoberFest Mombasa. On 22nd October 2021, we facilitated an OONI workshop (“How to measure Internet censorship”) for Kenyan civil society as part of the Swahilipot Hub event for HacktoberFest Mombasa.
OPTIMA 2.0 Network Measurement Training. On 21st and 28th October 2021, we attended Internews’ live sessions for the “Introduction to Network Measurement” and “OONI” training modules of the OPTIMA 2.0 training program, where we addressed participant questions pertaining to the training modules.
Bachchao Project test list event. On 9th and 10th October 2021, we participated in the Bachchao Project’s 2-day event (“India, Let’s Build the List”) where we gave a 1-hour presentation (“Introduction to Internet censorship”), demoed OONI’s new web platform for updating test lists, and helped facilitate the hands-on sessions for updating the Citizen Lab’s test list for India.
DIG Festival 2021. On 3rd October 2021, we participated in a panel discussion at the DIG Festival for investigative journalism in Modena, Italy, where we discussed OONI’s censorship measurement approach and algorithmic censorship.
Kenya Internet Governance Forum (KIGF) 2021 panel. On 21st September 2021, we participated as a speaker in a (pre-event) panel session at the Kenya Internet Governance Forum (KIGF) 2021, where we discussed OONI’s partnerships with digital rights groups in Africa to measure and respond to internet censorship events.
Access Now Twitter Space. On 15th September 2021, we participated as a speaker in Access Now’s Twitter Space (“Global Rise of Internet Shutdowns #KeepItOn”), where we discussed how OONI tools and data can be used for measuring the blocking of websites and apps, as well as OONI’s role in Access Now’s #KeepItOn campaign fighting internet shutdowns worldwide.
Access Now webinar. On 30th July 2021, we presented OONI as part of Access Now’s webinar (“#KeepItOn during an internet shutdown: How to measure, document, and circumvent network interference”), where we discussed how OONI’s tools and data can be used for measuring the blocking of websites and apps.
Nexa Center for Internet and Society 90th Seminar. On 28th July 2021, we presented OONI at the Nexa Center for Internet and Society, where we provided OONI updates on the state of internet censorship worldwide in 2020.
OONI Partner Training 2021. Between 28th June 2021 to 7th July 2021, we organized and hosted 2 online OONI Partner Training events, where we presented OONI tools and methodologies and collected community feedback.
RightsCon Online 2021. In June 2021, we participated in RightsCon 2021, where we had the opportunity to speak in the following 5 sessions:
Community Lab session: “Who are the perpetrators of internet shutdowns? What we documented in 2020 and beyond” (organized by Access Now’s #KeepItOn campaign), 7th June 2021
Strategy session: “Measuring internet disruptions during elections (and other political events)” (organized by OONI and CAIDA), 7th June 2021
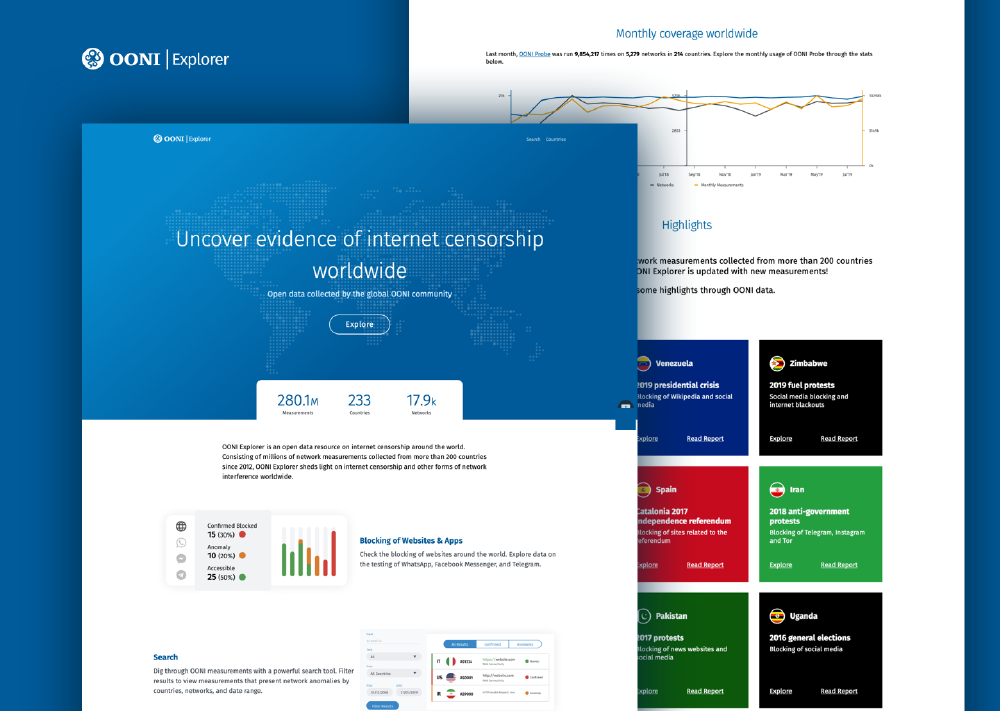
Tech demo: “Understanding internet censorship data through OONI Explorer” (organized by OONI), 10th June 2021
Panel: “Confronting threats from all sides: building the anti-censorship ecosystem” (organized by Internews), 10th June 2021
Community Lab session: “Prepare, prevent, resist: a guide for internet shutdown advocacy strategy and resilience” (organized by Internews), 11th June 2021
TechUp workshops. On 15th May 2021, we facilitated 2 online OONI workshops for civil society communities in India and in the Philippines as part of the TechUp event. During these 2 workshops, we presented OONI’s tools, methodologies, and dataset, and provided live demos explaining how participants can use OONI Explorer to track censorship events worldwide in real-time.
Stockholm Internet Forum 2021. On 12th May 2021, we participated as a speaker on a panel discussion (“#KeepItOn: Governments weaponizing Internet shutdowns”) at the Stockholm Internet Forum 2021, where we presented OONI’s work and discussed how OONI has supported the advocacy efforts of the #KeepItOn campaign in fighting internet shutdowns around the world.
Nexa Center for Internet and Society 87th Seminar. On 28th April 2021, we participated as a speaker at the 87th Nexa Lunch Seminar (titled “The risks of digital sovereignty”).
MozFest 2021. On 17th March 2021, we facilitated a session (“Exploring Internet censorship through OONI data”) at MozFest 2021 where we demoed OONI Explorer and explained how human rights defenders can use the platform to investigate internet censorship around the world.
DigitalReach webinar. On 17th March 2021, we participated as a speaker on DigitalReach’s webinar, “From Beijing with Love: The Internet Firewall in Southeast Asia”, where we presented OONI’s methodologies and explained how civil society groups in Southeast Asia can use OONI Probe and OONI data to investigate internet censorship.
OutRight Action International webinar. On 24th February 2021, we participated in OutRight Action International’s webinar (“Censored: How LGBTIQ People And Activists Are Threatened By - And Surviving In - Restrictive And Repressive Digital Environments”) where we discussed OONI’s collaboration with OutRight Action International and the Citizen Lab on investigating LGBTIQ website censorship in Russia, Iran, Saudi Arabia, UAE, Malaysia, and Indonesia.
2021 DNS Privacy Workshop of the NDSS Symposium. On 1st February 2021, we presented our research paper, “Measuring DoT/DoH Blocking Using OONI Probe: a Preliminary Study”. In particular, we presented our new DNSCheck experiment and measurement results from the testing of 123 DoT/DoH services (corresponding to 461 TCP/QUIC endpoints) in Kazakhstan, Iran, and China.
We also presented OONI as part of a number of other private online workshops, training, and events. We thank community members for their participation and invaluable feedback!
OONI-verse
In 2021, the OONI community continued to contribute many measurements from most countries and territories around the world.
Some highlights of OONI activities by our community in 2021 include:
PiProbe. Our Venezuelan partners, Venezuela Inteligente, created a new OONI Probe distribution for Raspberry Pis, called “PiProbe”.
Report on media censorship during 2021 regional elections in Venezuela. Venezuela Inteligente published a report which documents the blocking of media websites amid Venezuela’s 2021 regional elections. Their report makes use of OONI data, among other data sources.
OONI Probe integration into Murakami. Measurement Lab (M-Lab) integrated OONI Probe into their Murakami internet measurement tool. We are grateful for this integration, as it will help increase OONI measurement coverage from more vantage points!
OONI Probe integration into iThena. iThena is a distributed computation and measurement project based on the Berkeley Open Infrastructure for Network Computing (BOINC) platform. The integration of OONI Probe into the iThena platform has helped boost OONI measurement coverage worldwide!
Report on the blocking of social networking sites in Sudan. Community members from Sudan published a report which documents the blocking of social networking sites in Sudan based on OONI data.
NetDAN assistive tool. Unwanted Witness launched the NetDAN assistive tool which notifies people with visual disabilities of network disruptions in Uganda based on OONI data. NetDAN detects and audibly informs the users about the connectivity status of the most commonly used websites and applications in Uganda, using OONI data.
Freedom on the Net 2021 reports. Freedom House published its annual Freedom on the Net country reports. OONI data was cited in (at least) the Freedom on the Net reports for the following countries: Uganda, Italy, Myanmar, Azerbaijan, Iran, Malaysia, Saudi Arabia, Zambia, Brazil, Colombia, Jordan, and Ethiopia.
OONI training in Tanzania. In July 2021, Zaina Foundation organized and facilitated an Internet Shutdown Training for human rights defenders in Tanzania, which included several OONI training sessions. Zaina Foundation shared community feedback with us and coordinated with local communities on translating OONI Probe to Swahili.
OONI documentation in Farsi. Iranian community members created detailed and comprehensive documentation which explains OONI tools and methodologies in Farsi.
OONI Probe video tutorial in Spanish. Our Bolivian partners, Fundación Internet Bolivia, created a video tutorial in Spanish where they present OONI and explain OONI Probe, providing a live demo of using the tool.
Report on media censorship in Venezuela. Venezuela Inteligente published a report which documents the blocking of media websites in Venezuela. Their report makes use of OONI data, among other data sources.
Paradigm Initiative’s Ayeta Digital Rights Toolkit. Our Nigerian partner, Paradigm Initiative, published the Ayeta Digital Rights Toolkit, which aims to address the growing need to safeguard digital rights defenders, journalists, whistle blowers, and others working with sensitive information in the global South. OONI is featured as a recommended tool under the “Measuring Internet Shutdowns and Censorship” section of the Ayeta Digital Rights Toolkit.
OONI Probe Command Line Interface (CLI) guide in Spanish. A community member (Jacobo Nájera) wrote and published a guide in Spanish which explains how to install and use the OONI Probe Command Line Interface (CLI).
2020 Annual Report on Digital Rights in Venezuela. Our Venezuelan partners, IPYS Venezuela, published their 2020 Annual Report on Digital Rights in Venezuela, which made use of OONI data.
Report on the blocking of websites in Egypt. Our Egyptian partners, Masaar - Technology and Law Community, published a research report documenting the techniques and laws around the blocking of websites in Egypt. As part of this report, they made use of OONI data.
OONI training in Cameroon. Our Cameroonian partner, COMPSUDEV, collaborated with AfroLeadership on organizing and facilitating a 2-day training event (“Building Evidence for Internet Rights Advocacy”) for civil society groups in Cameroon. As part of this training event, they facilitated OONI workshops with the goal of introducing participants to OONI’s tools, methodologies, and dataset.
OONI guide by Fundación Karisma. Our Colombian partner, Fundación Karisma, wrote and published a short OONI guide in Spanish.
Micro-course on Internet censorship. Asuntos del Sur launched Plataforma Inteligencia de Riesgos, an online platform that provides micro-courses on digital security and digital rights related topics. This platform features a micro-course on internet censorship (including a video about OONI Probe), which we had the opportunity to contribute. As these micro-courses are primarily geared towards civil society groups in Latin America, the materials include Spanish translations.
Report on the blocking of currency exchange rate websites in Lebanon. SMEX published an article on the blocking of currency exchange rate websites in Lebanon, citing OONI data.
OONI Probe localization. Thanks to the Localization Lab community, the OONI Probe app has been translated to the following 21 languages: Chinese, Russian, Arabic, Persian, Spanish, French, Hindi, Indonesian, Thai, Turkish, Icelandic, Italian, Dutch, Portuguese, Catalan, German, Greek, Romanian, Slovak, Albanian, and Swahili.
We thank our community for their amazing OONI efforts!
2022
We have many exciting projects lined up for 2022!
Some highlights include:
OONI Measurement Aggregation Toolkit (MAT). We aim to publicly launch our Measurement Aggregation Toolkit (MAT) in 2022 to enable the internet freedom community to produce custom charts based on aggregate views of OONI data, supporting research and rapid response efforts to emergent censorship events.
New web platform for community contributions to test lists. In 2022, we aim to publicly launch our new web platform that will enable community members to easily review and contribute to the Citizen Lab test lists (without having to use GitHub).
New browser-based censorship measurement tool. In 2022, we aim to release OONI Probe Web to simplify the process of testing websites during urgent censorship events. This will complement the OONI Probe apps and serve needs related to rapid response.
New website measurement test. We aim to ship our new website measurement test as part of the OONI Probe apps, significantly improving the quality of website censorship testing and resulting measurements.
New network measurement tests. We aim to ship new experiments (such as the Tor Snowflake pluggable transport test) developed in 2021 as part of the OONI Probe apps, and develop new tests!
Backend infrastructure overhaul. To improve the performance of our services and to enhance our data analysis capabilities, we are migrating over to new infrastructure. Throughout 2022, we will work on improving our data processing capabilities and making significant performance optimizations in our backend infrastructure.
New community resources. We aim to publish new resources to support OONI community engagement efforts, including multimedia content.
More research reports, workshops, and training. We will continue to collaborate with community members on investigating censorship events worldwide and documenting them through the publication of research reports. We will also continue to engage communities through OONI workshops and training.
Our above priorities for 2022 have been informed by community feedback collected over the years (as well as in response to the dynamic censorship environment worldwide). If there are additional areas that you think we should prioritize, please don’t hesitate to let us know.
If you would like to support our work, please consider donating to OONI.
Warm thanks to the global OONI community for supporting our work throughout 2021!
We are grateful to every OONI Probe user out there, and we’re excited for 2022. Stay tuned! And above all, stay safe.